Single Sign-On
OAuth is an authorization protocol that supports SSO implementations with various grant types. DolphinDB supports three of them: authentication code grant (for Web interface), implicit grant (for Web interface), and client credentials grant (for APIs). To enable OAuth SSO, users need to obtain the permissions for both the third-party website and the DolphinDB server. After successful login, they can use the third-party services on the web interface.
This section briefly introduces the procedure for single sign-on to GitHub.
Step 1: Enable OAuth on the Third-Party Website
Create an OAuh app on GitHub. For specific steps, refer to Creating an OAuth app.
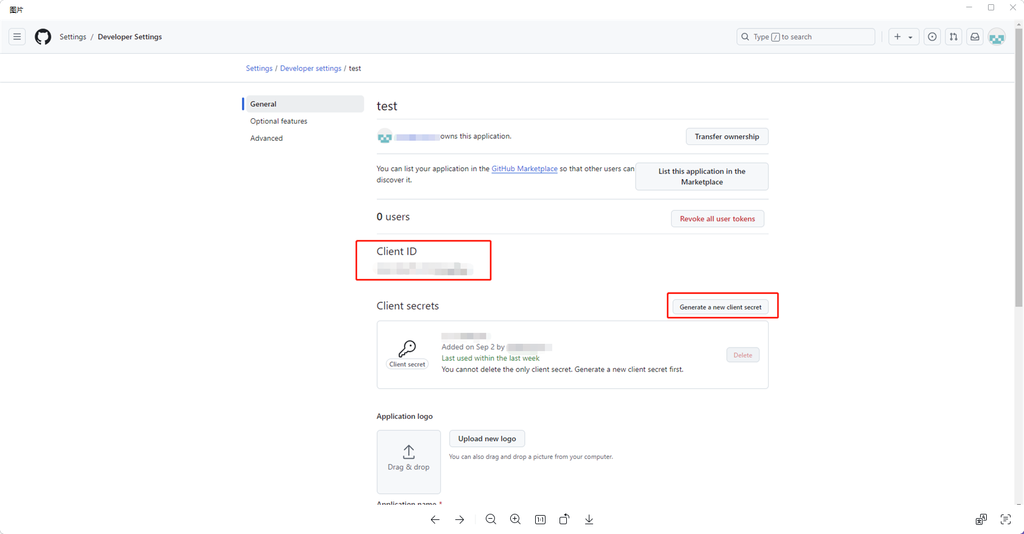
Once the OAuth app is successfully created, you will see the interface below, in which the "Client ID" and "Client secrets" (click Generate a new client secret) are displayed.
Step 2: Configure OAuth Parameters in DolphinDB
Specify the client ID and password in DolphinDB Web interface as the above-mentioned "Client ID" and "Client secrets".
DolphinDB provides a series of configuration parameters for OAuth SSO. Users can configure these parameters in the configuration file of DolphinDB server or in the Config tab of the web interface.
Note: To use OAuth in a cluster, users need to add the relevant configuration parameters in controller.cfg and cluster.cfg on all nodes.
Here is an example of setting OAuth configuration parameters:
oauth = 1
oauthWebType = authorization code
oauthAuthuri = "https://github.com/login/oauth/authorize"
oauthClientld = xxxxxx
oauthClientSecret = xxxxxx
oauthTokenUri = "https://github.com/login/oauth/access_token"
oauthUserUri = "https://api.github.com/user"
oauthUserField = login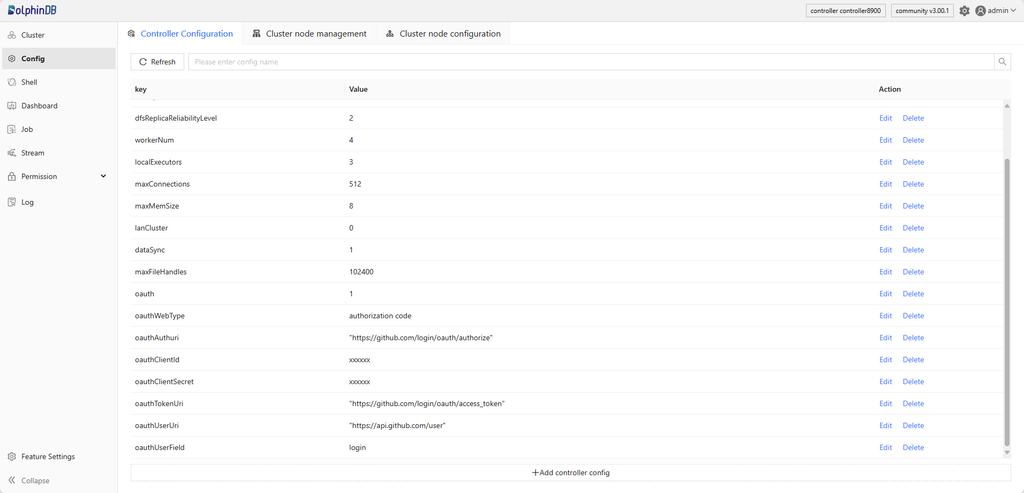
Step 3: Log into a Third-Party Account on DolphinDB Web
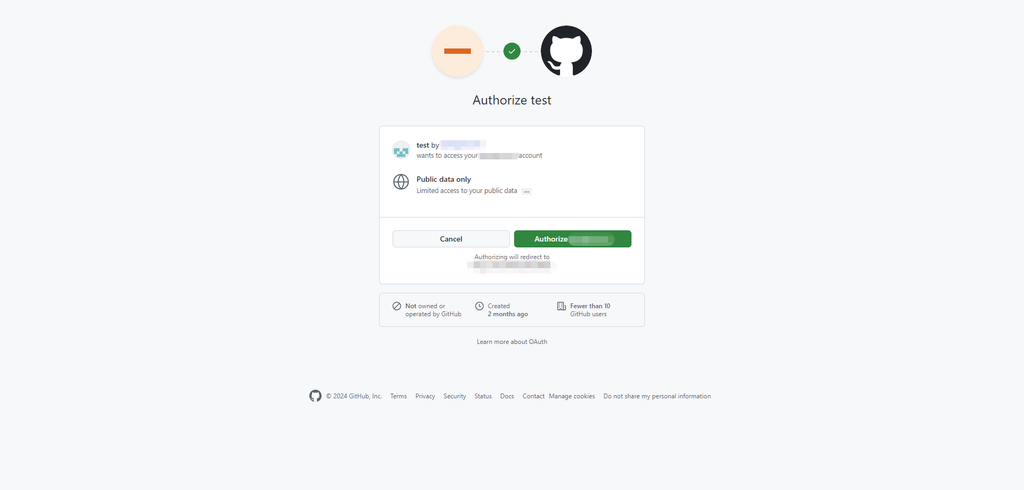
After the configuration is complete, when logging in from the Web interface, the page will redirect to the third-party account authorization interface. Once authorized, the page will redirect back to the original login page.
If the username displayed on the web interface is the authorized third-party username, the OAuth login is successful.
